Cracker Probing-Eyes®
It is a tool for checking and assessing vulnerabilities in the internal network structure of an organization at each layer, both in standard (Basic Scan) and full scan modes.
This tool can assess vulnerabilities at different layers, such as the network infrastructure layer, the layer between the operating system and applications (Operating System Middleware), the layer connecting to external public websites (Website Public), and even the layer of internal applications used within the organization.
The Cracker Probing-Eyes® tool functions like a large database or library that stores and updates information about various vulnerability cases using deep learning AI technology. This information is stored in a library format with IDs as references. If the tool scans the system and finds cases that match or closely resemble each other, it will generate a list to report the risk level of each case in order of importance.



Have you ever encountered these problems?
- Have you ever experienced a system breach or data breach by hackers?
- Concerned about the security level of company web applications and software?
- Received questions from customers regarding confidence in the organization's security system?
- Need to check for vulnerabilities in the internal network structure of the organization?
Check and assess your situation to take preventive action before it's too late!
Today, you will encounter increasingly complex and sophisticated attack methods continuously.
Your systems will become vulnerable every day.
Vulnerabilities growing every day
Anyone, anything can be a target
Know the status of your system and
take necessary measures!
You can use the source code diagnosis at any time even at home or office by simply uploading the source code of the application to Cracker Probing-Eyes®
From our recent checks, we found that more than 80% of the systems have vulnerabilities, with 20% being critical vulnerabilities at a crisis level! The main cause of these vulnerabilities is refusal to update various software within the organization, accounting for 60%
So no matter how confident you are that your system is highly secure, you must not forget that malicious actors are constantly evolving. Regular updates, continuous monitoring, and addressing various vulnerabilities will help keep you safe from cyberattacks.
With the current situation of incidents and system vulnerabilities increasing continuously, vigilance and regular assessment of our infrastructure system is another way to help us survive cyberattacks. Even though cyberattacks may seem superficial and not very intimidating at first glance, when you compare the number of incidents and the value of the damage caused, the impact is not insignificant at all. The threats in this digital transformation era are much closer to us than we think.
"Ignorance is the biggest vulnerability" and "knowledge" are the first and foremost important aspects of cybersecurity."
Vulnerability assessment allows you to monitor the security status of your system in the face of ever-changing threats, enabling you to apply appropriate measures promptly.
The operation process of the automatic vulnerability scanning tool
Cracker Probing-Eyes®
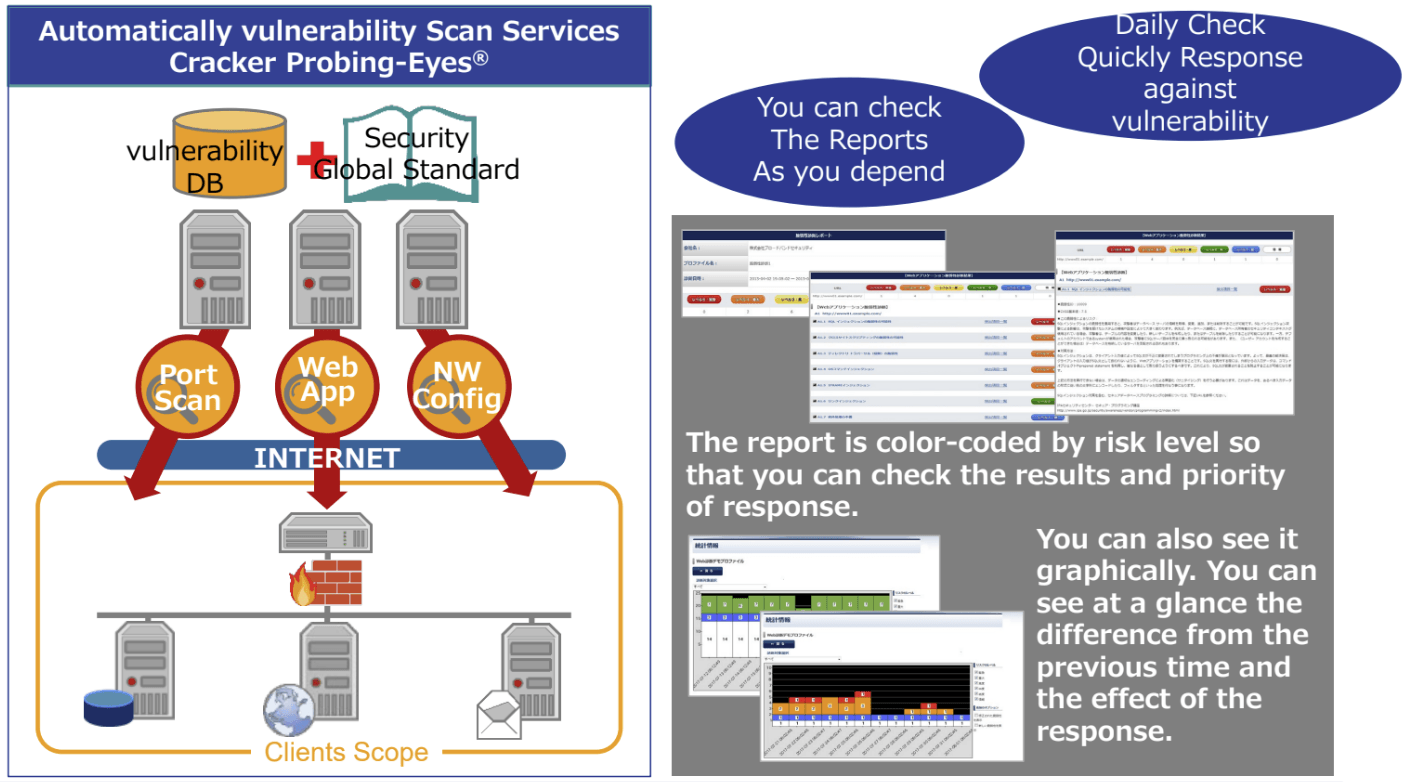
1. The tool operates by inspecting data from the database and comparing it to security information from Security Global Standards.
2. The tool scans various vulnerabilities of port connections, web applications, and internal organization networks.
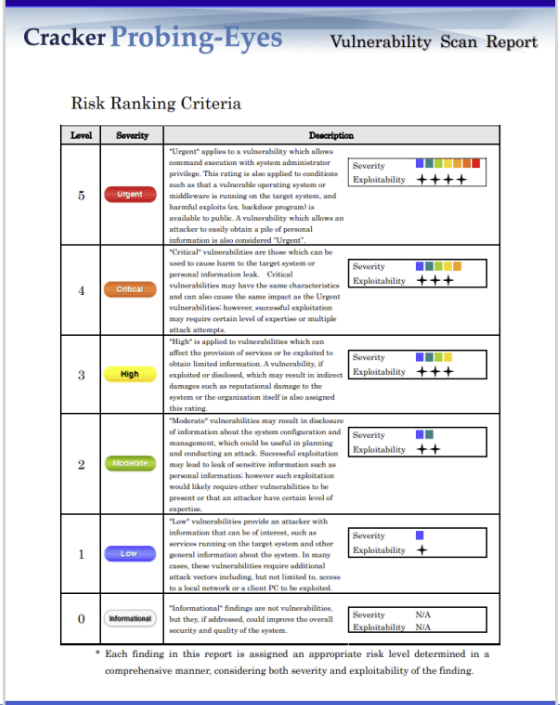
3. The report output for each diagnosis is color-coded by risk level, allowing you to check the diagnosis results and the importance of countermeasures at a glance.
3.1. The report will have color codes according to the risk level, allowing you to check the results and prioritize fixes.
3.2. Graphic reports will enable you to quickly see differences in each scan or post-fix results.
4. Automated vulnerability tools that you can diagnose every day quickly discover new vulnerabilities and the diagnosis results can be checked on the web at any time.
Cracker Probing-Eyes® Features a comprehensive coverage of OWASP TOP10 vulnerabilities.
OWASP TOP10 is one of OWASP’s projects that ranks the top 10 security risks. Initially, it used to rank only the top 10 web-related risks. Later, other projects were added, such as the top 10 risks for mobile applications, IoT, and the Cloud.
For web application and network vulnerability scanning tool, Cracker Probing-Eyes® has the entire OWASP TOP10 database, and the tool itself receives regular database updates. This means that even with new risks emerging from any project, this Cracker Probing-Eyes® tool will undoubtedly detect these vulnerabilities.
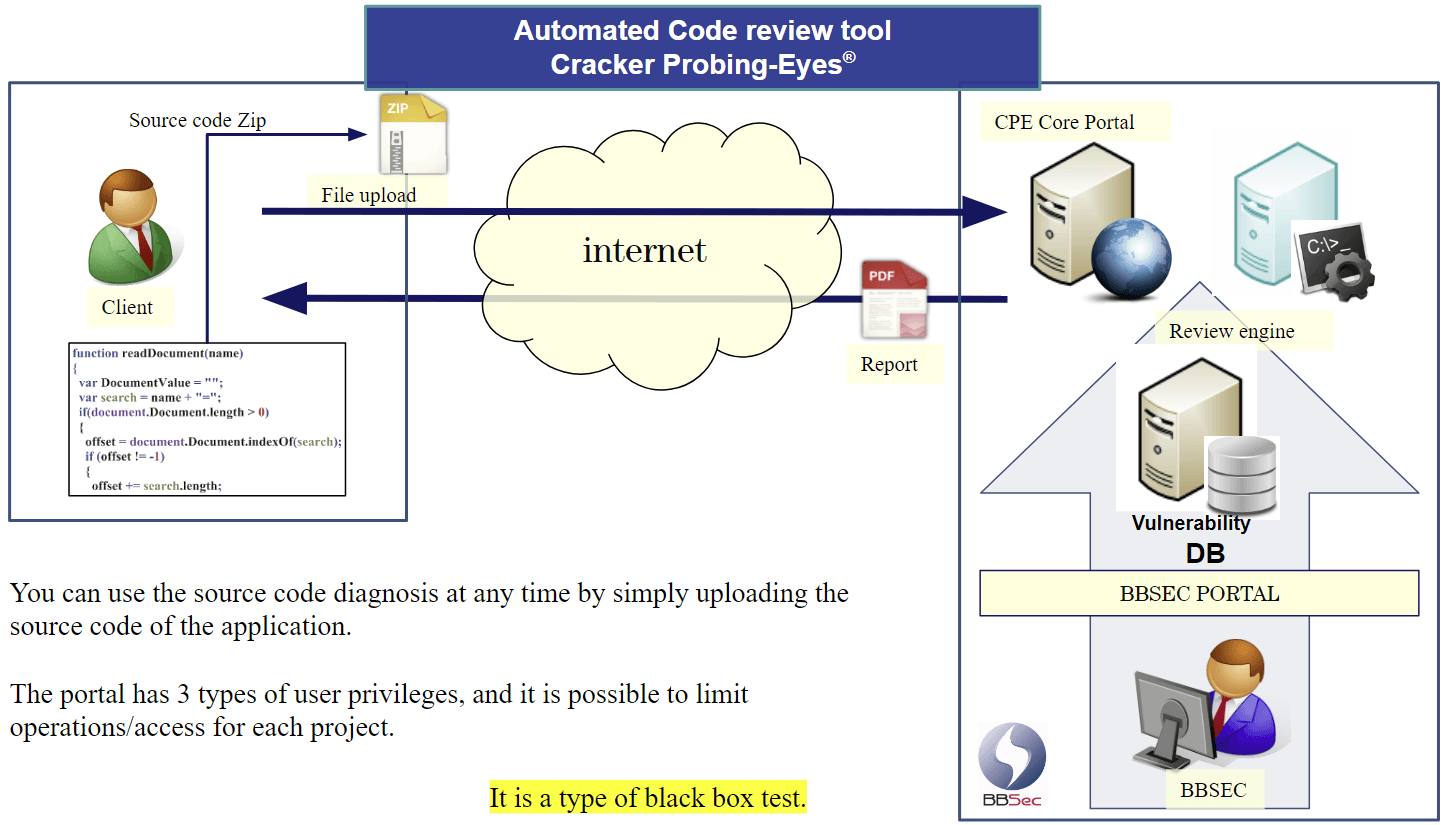
Cracker Probing-Eyes® can also analyze and assess vulnerabilities and the quality of source code using both static analysis (analysis of the running application) and dynamic analysis (analysis of uploaded source code of applications to the “Cracker Probing-Eyes® Core” portal, through the services of our partner company, BBSec).
You can easily analyze the security and quality of your source code at any time during app development, whether it’s from home, the office, or anywhere in the world. In addition to viewing the analysis results, you can also generate reports after the analysis is completed.
Sample Report of Cracker Probing-Eyes®
Left: Criteria
Criteria
Right: Fact and Finding
Fact and Finding

Let's learn how to prepare and effectively deal with various system vulnerability attacks within the organization.

Special privileges
– Try using Cracker Probing-Eyes® once for free!
Click to download the full-service documentation → CPE Cracker Probing-Eyes®
Contact us for service
Protect your business with our state-of-the-art IT solutions!